LDAP Reconnaissance
Reconnaissance is an important part of any successful attack. There are two key forms: initial or external reconnaissance that is performed before an adversary infiltrates an organization, and internal reconnaissance where they discover additional information and context about the organization’s environment.
LDAP reconnaissance is an internal reconnaissance technique attackers use to discover users, groups and computers in Active Directory. They use LDAP queries to increase their knowledge of the environment, which can help them find targets and plan the next stages of their attack. Because this technique is used by adversaries who have already infiltrated an organization, it is an internal (rather than external) reconnaissance technique.
Performing Reconnaissance using LDAP
Obtain a foothold
[attacker@machine ~]$ spray.sh -cisco vpn.org.com usernames.txt passwords.txt 1 35
Valid Credentials joed Summer2020Perform reconnaissance using LDAP
PS> Import-Module ActiveDirectory
PS> Get-ADObject -LDAPFilter "(&(objectClass=user)(description=*pass*))" -property * | Select-Object SAMAccountName, Description, DistinguishedName
SAMAccountName Description DistinguishedName
-------------- ----------- -----------------
Alice Password: P@ssw0rd123! CN=Alice,OU=Users,DC=domain,DC=com
PS> Use information to further objectives
The graphic below illustrates an example. Suppose an attacker gains the credentials for the user account Alice. That account has
WriteDACL and WriteOwner permissions to the user Eve, which means Alice can grant herself access to Eve’s account. Eve has rights to reset the password of the account Bob, and Bob has permissions (granted through AdminSDHolder propagation) to modify the Domain Admins group. Therefore, finding Alice’s password was very valuable the adversary!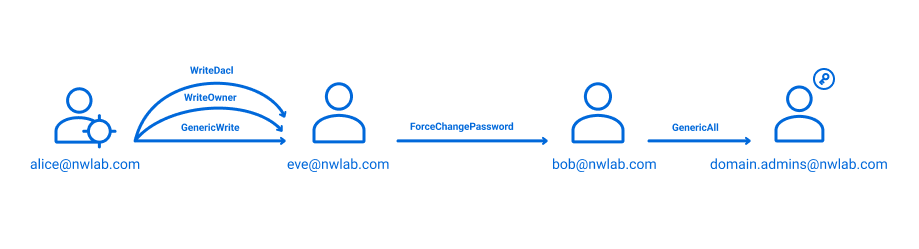
Result
After collecting data withSharpHound.exe -C All the adversary can load the data set into BloodHound to explore pathways to domain dominance.
Detect, Mitigate and Respond
Monitoring network traffic received by domain controllers for specific LDAP queries can help you detect adversary activity. The following table shows a small sampling of the kinds of queries that should be infrequent in normal operation but can provide strong signals of adversary activity:
| Query | Information Collected |
| (&(ObjectClass=user)(servicePrincipalName=*)) | All user objects that have a ServicePrincipalName configured |
| (userAccountControl:1.2.840.113556.1.4.803:=65536) | Objects that have Password Never Expires set |
| (userAccountControl:1.2.840.113556.1.4.803:=4194304) | Objects that do not require Kerberos pre-authentication |
| (sAMAccountType=805306369) | All computer objects |
| (sAMAccountType=805306368) | All user objects |
| (userAccountControl:1.2.840.113556.1.4.803:=8192) | All domain controller objects |
| (primaryGroupID=512) | All Domain Admins using PrimaryGroupID |
If an adversary’s presence is confirmed:
- Reset the password and disable the user account performing reconnaissance.
- Quarantine the source computer for forensic investigation and eradication and recovery activities.
Monitoring network traffic received by domain controllers for specific LDAP queries can help you detect adversary activity. The following table shows a small sampling of the kinds of queries that should be infrequent in normal operation but can provide strong signals of adversary activity:
| Query | Information Collected |
| (&(ObjectClass=user)(servicePrincipalName=*)) | All user objects that have a ServicePrincipalName configured |
| (userAccountControl:1.2.840.113556.1.4.803:=65536) | Objects that have Password Never Expires set |
| (userAccountControl:1.2.840.113556.1.4.803:=4194304) | Objects that do not require Kerberos pre-authentication |
| (sAMAccountType=805306369) | All computer objects |
| (sAMAccountType=805306368) | All user objects |
| (userAccountControl:1.2.840.113556.1.4.803:=8192) | All domain controller objects |
| (primaryGroupID=512) | All Domain Admins using PrimaryGroupID |
If an adversary’s presence is confirmed:
- Reset the password and disable the user account performing reconnaissance.
- Quarantine the source computer for forensic investigation and eradication and recovery activities.
MITRE ATT&CK® and ATT&CK® are registered trademarks of The MITRE Corporation.